How to Troubleshoot Active Directory Across Firewalls
Do you have an Active Directory server in a Datacenter separated by a VPN? Or simply on a different VLAN with a firewall between? Perhaps you simply keep the Windows firewalls enabled…
If so, you have likely experienced issues with communications between the AD servers at some point. There are a few guides out there to help you, but most of them are of limited help unless you work with both AD and firewalls every day.
So what we are doing is compiling a program that you can use to query all your DCs and will output results of multiple diagnostics tools.
Until that is released, you can use some existing tools to validate:
PortQryV2 – This tool allows you to query common ports using TCP or UDP.
DCPortTest.cmd – This script tests several common AD ports and outputs the results. Note you will need a file named server.txt with the list of servers to test (one per line) in the same directory as this CMD file and the PortQry.exe file. Output is stored in DC_PORTQRY.TXT in the same directory. If the output lists FILTERED for a port, then you need to fix your firewall. Note I have copied the code from that site at the bottom of this article because their site messed up the double quotes and it won’t work without replacing them.
repadmin /showrepl – Command line command which will show the results of every AD server replicating against. If you see anything other than “…was successful”, you need to look into it.
repadmin /syncall – Command line command forces replication to all domain controllers immediately. If there are any errors, look into the error with the server the error occurred with.
dcdiag – Command line command tests numerous connectivity and functional areas of the AD servers. Look for any failure or error.
Most of the times, errors from these commands point to either a problem with DNS or your Firewall. Understanding DNS is beyond scope of this article, we are concentrating on Firewall issues.
Be aware, if a server is listed as Tombstoned, then it must be demoted, Metadata cleaned up, and then promoted to restore operation.
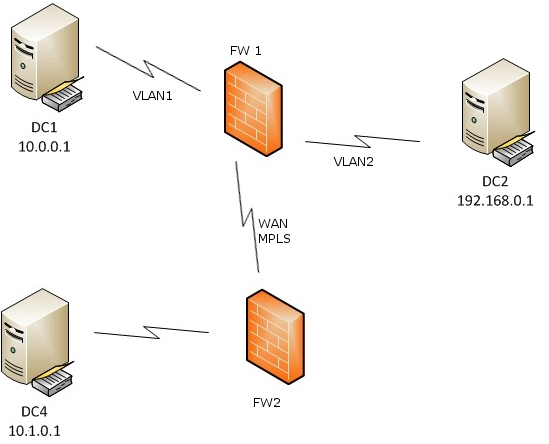
Take the below image. We have 3 AD servers. DC1 and DC2 are in the same network, on different VLANs separated by firewall FW1. DC4 is on a different Network separated by an MPLS link with an additional firewall, FW2. We are going to assume there is No NAT occurring on the firewalls to make the discussion simpler. We will also assume stateful firewalls.
FW1 needs two rules allowing traffic for DC1 to DC2 and DC2 to DC1. You might ask why, since the firewalls are stateful? Simple. Either DC can initiate the communication, and we want to allow it regardless of which DC does.
Now you also need rules on both FW1 and FW2 allowing DC1 and DC2 to DC4, and allowing DC4 to DC1 and DC2.
Your next question hopefully is: For what ports? Glad you asked; there’s quite a few. I’ve listed details below the image.
| Protocol and Port | AD and AD DS Usage | Type of traffic | ||
|---|---|---|---|---|
| TCP and UDP 389 | Directory, Replication, User and Computer Authentication, Group Policy, Trusts | LDAP | ||
| TCP 636 | Directory, Replication, User and Computer Authentication, Group Policy, Trusts | LDAP SSL | ||
| TCP 3268 | Directory, Replication, User and Computer Authentication, Group Policy, Trusts | LDAP GC | ||
| TCP 3269 | Directory, Replication, User and Computer Authentication, Group Policy, Trusts | LDAP GC SSL | ||
| TCP and UDP 88 | User and Computer Authentication, Forest Level Trusts | Kerberos | ||
| TCP and UDP 53 | User and Computer Authentication, Name Resolution, Trusts | DNS | ||
| TCP and UDP 445 | Replication, User and Computer Authentication, Group Policy, Trusts | SMB,CIFS,SMB2, DFSN, LSARPC, NbtSS, NetLogonR, SamR, SrvSvc | ||
| TCP 25 | Replication | SMTP | ||
| TCP 135 | Replication | RPC, EPM | ||
| TCP Dynamic* Win 2003: 1025 – 5000 Win 08-12: 49152 – 65535 |
Replication, User and Computer Authentication, Group Policy, Trusts | RPC, DCOM, EPM, DRSUAPI, NetLogonR, SamR, FRS | ||
| TCP 5722 | File Replication | RPC, DFSR (SYSVOL) | ||
| UDP 123 | Windows Time, Trusts | Windows Time | ||
| TCP and UDP 464 | Replication, User and Computer Authentication, Trusts | Kerberos change/set password | ||
| UDP Dynamic* Win 2003: 1025 – 5000 Win 08-12: 49152 – 65535 |
Group Policy | DCOM, RPC, EPM | ||
| UDP 138 | DFS, Group Policy | DFSN, NetLogon, NetBIOS Datagram Service | ||
| TCP 9389 | AD DS Web Services | SOAP | ||
| UDP 67 and UDP 2535 | DHCP
|
DHCP, MADCAP | ||
| UDP 137 | User and Computer Authentication, | NetLogon, NetBIOS Name Resolution | ||
| TCP 139 | User and Computer Authentication, Replication | DFSN, NetBIOS Session Service, NetLogon | ||
| UDP 5005 | Microsoft Real Time Control Protocol. Note while this is not officially on MS list of required ports for AD, I had some replication failures without it on Server 2012 R2. | RTCP |
* – You can Limit these Dynamic ports. Refer to this article. Basically, use this command for TCP/UDP IPv4/IPv6:
netsh int <ipv4|ipv6> set dynamic <tcp|udp> start=number num=range
The below example commands sets the dynamic port range for TCP and UDP on IPv4. The start port is 10000, and the total number of ports is 1000 so you end up port ranges of 10000-10999:
netsh int ipv4 set dynamicport tcp start=10000 num=1000
netsh int ipv4 set dynamicport udp start=10000 num=1000
DCPortTest.cmd code. Copy and paste into notepad and save as a CMD or BAT file:
:::::::::::::::::::::::::::: BEGIN SCRIPT :::::::::::::::::::::::::
@ECHO OFF
:: NAME: DCPortTest.CMD v1.0
:: DATE: 03/29/2009
:: PURPOSE: Test connectivity from one DC to one or more remote DCs
:: using PORTQRY utility.
:: The SERVERS.TXT contains a list of servers (one server per line)
:: to check connectivity to.
ECHO DATE: %DATE% > DC_PORTQRY.TXT
ECHO TIME: %TIME% >> DC_PORTQRY.TXT
ECHO USER: %USERNAME% >> DC_PORTQRY.TXT
ECHO COMPUTER: %COMPUTERNAME% >> DC_PORTQRY.TXT
ECHO. >> DC_PORTQRY.TXT
ECHO. >> DC_PORTQRY.TXT
ECHO. >> DC_PORTQRY.TXT
FOR /F "tokens=1" %%i in (servers.txt) DO (
ECHO :::::::::::::::::::::: %%i :::::::::::::::::::::::::: >> DC_PORTQRY.TXT
ECHO Testing %%i
ECHO. >> DC_PORTQRY.TXT
PORTQRY -n %%i -e 88 -p TCP | findstr /i "88" >> DC_PORTQRY.TXT
PORTQRY -n %%i -e 445 -p TCP | findstr /i "445" >> DC_PORTQRY.TXT
PORTQRY -n %%i -e 389 -p TCP | findstr /i "389" >> DC_PORTQRY.TXT
PORTQRY -n %%i -e 3268 -p TCP | findstr /i "3268" >> DC_PORTQRY.TXT
PORTQRY -n %%i -e 135 -p TCP | findstr /i "135" >> DC_PORTQRY.TXT
ECHO. >> DC_PORTQRY.TXT
ECHO. >> DC_PORTQRY.TXT
)
 Note
Note